Quality has long been a concern of businesses, as it should be for systems analysts in the analysis and design of information systems. The user of the information system is the single most important factor in establishing and evaluating its quality. … [Read more...] about Quality Assurance and Implementation
Quality Assurance and Implementation
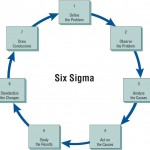
The Total Quality Management Approach – Six Sigma
Total quality management (TQM) is essential throughout all the systems development steps. According to Evans and Lindsay (2004), the primary elements of TQM are meaningful only when occurring in an organizational context that supports a comprehensive … [Read more...] about The Total Quality Management Approach – Six Sigma
Responsibility for Total Quality Management
Practically speaking, a large portion of the responsibility for the quality of information systems rests with systems users and management. Two things must happen for TQM to become a reality with systems projects. First, the full organizational … [Read more...] about Responsibility for Total Quality Management
Top-Down Systems Design and Development
Many companies first introduced computer systems on the lowest level of the organization. This is where the immediate benefits to computerization are most observable and cost-effective. Businesses often take this approach to systems development by … [Read more...] about Top-Down Systems Design and Development
Using Structure Charts to Design Modular Systems
Once the top-down design approach is taken, the modular approach is useful in programming. This approach involves breaking the programming into logical, manageable portions, or modules. This kind of programming works well with top-down design because … [Read more...] about Using Structure Charts to Design Modular Systems
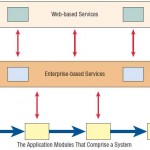
Service-Oriented Architecture (SOA)
Modular development has led to a concept called service-oriented architecture (SOA), but one that is very different from the modules in the structure chart. Instead of being hierarchical like the top-down approach found in structure charts, the SOA … [Read more...] about Service-Oriented Architecture (SOA)
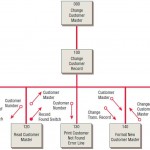
Documentation Approaches
The total quality assurance effort requires that programs be documented properly. Software, systems, and formal and informal procedures need to be documented so that systems can be maintained and improved. Documentation allows users, programmers, and … [Read more...] about Documentation Approaches
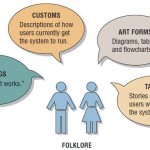
The FOLKLORE Documentation Method
FOLKLORE is a systems documentation technique that was created to supplement some of the techniques just covered. Even with the plethora of techniques available, many systems are inadequately documented or not documented at all. FOLKLORE gathers … [Read more...] about The FOLKLORE Documentation Method
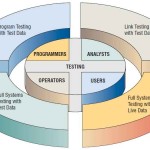
The Testing Process – Quality Assurance
All the system’s newly written or modified application programs—as well as new procedural manuals, new hardware, and all system interfaces—must be tested thoroughly. Haphazard, trial-and-error testing will not suffice. Testing is done throughout … [Read more...] about The Testing Process – Quality Assurance
Maintenance Practices & Auditing – Quality Assurance
Your objective as a systems analyst should be to install or modify systems that have a reasonably useful life. You want to create a system whose design is comprehensive and farsighted enough to serve current and projected user needs for several years … [Read more...] about Maintenance Practices & Auditing – Quality Assurance
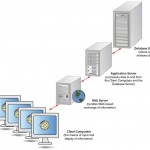
Implementing Distributed Systems – Client-Server Technology
If the reliability of a telecommunications network is high, it is possible to have distributed systems for businesses, a setup that can be conceived of as an application of telecommunications. The concept of distributed systems is used in many … [Read more...] about Implementing Distributed Systems – Client-Server Technology
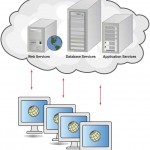
Cloud Computing – Distributed Systems
The most rapidly growing type of computing is cloud computing. Cloud computing has been described as a metaphor for the Internet, since the Internet is often drawn as a cloud in network diagrams. Using cloud computing, organizations and individual … [Read more...] about Cloud Computing – Distributed Systems
Network Modeling – Distributed Systems
Because networking has become so important, the systems designer needs to consider network design. Whether a systems designer gets involved with decisions about the configurations of networks—or whether he or she worries about hardware such as … [Read more...] about Network Modeling – Distributed Systems
Training Users/ Strategies & Guidelines
Systems analysts engage in an educational process with users that is called training. Throughout the systems development life cycle, the user has been involved so that by now the analyst should possess an accurate assessment of the users who must be … [Read more...] about Training Users/ Strategies & Guidelines
Conversion to a New System
A third approach to implementation is physically converting the old information system to the new or modified one. There are many conversion strategies available to analysts, and also a contingency approach that takes into account several user and … [Read more...] about Conversion to a New System
Security Concerns for Traditional and Web-Based Systems
Security of computer facilities, stored data, and the information generated is part of a successful conversion. Recognition of the need for security is a natural outgrowth of the belief that information is a key organizational resource, as discussed … [Read more...] about Security Concerns for Traditional and Web-Based Systems
Disaster Recovery Planning – Quality Assurance
No matter how diligently you and your organizational colleagues work to ensure the security and stability of systems, all employees and systems are inevitably vulnerable to some kind of natural or human-made disaster that threatens security as well … [Read more...] about Disaster Recovery Planning – Quality Assurance
Evaluation Techniques & Information System Utility Approach
Throughout the systems development life cycle, the analyst, management, and users have been evaluating the evolving information systems and networks to give feedback for their eventual improvement. Evaluation is also called for following system … [Read more...] about Evaluation Techniques & Information System Utility Approach
Evaluating Corporate Web Sites
Evaluating the corporate Web site that you are developing or maintaining is an important part of any successful implementation effort. Analysts can use the information system utility approach previously described to assess the aesthetic qualities, … [Read more...] about Evaluating Corporate Web Sites